Cyber Security Framework
The University’s policies on cyber security are governed in a hierarchical fashion as follows (refer to the diagram below).
- IT Acceptable Use and Security Policy (ITAUSP): this is the overarching policy managed under the University’s Policy Framework and articulates the fundamental principles on fair, equitable and secure use of University’s IT systems.
- There are currently two Procedures that support the ITAUSP, also managed under the University’s Policy Framework:
- IT Acceptable Use Procedures: expands on the ITAUSP for matters related to how end users are expected to use University IT for performing their learning, teaching, research, and operational activities.
- IT Security Procedures: expands upon the ITAUSP for technical controls to ensure consistent security controls for identities, workstations, servers, and applications. The audience for this procedure is mainly custodians who implement and maintain IT systems.
- The CSF security standards: provide more concrete technical directives by expanding on the security requirements expressed in the ITAUSP and the two procedures above. All IT Custodians, including ITDS and Distributed and Specialist IT custodians must understand and comply with these standards, or otherwise have exemptions approved by ITDS where compliance is not possible or practical.
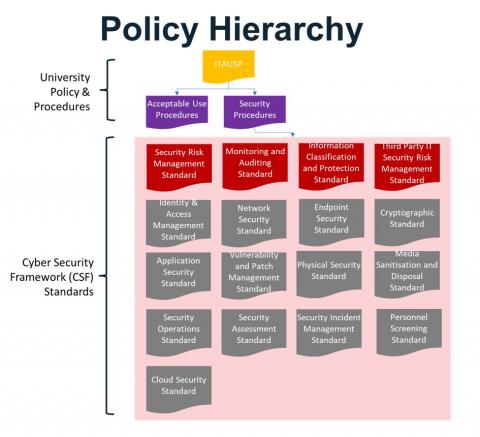
Cyber Security Framework (CSF) Standards
Refer to the links below for the CSF standards that have been approved by the Information Technology and Digital Services Governance Committee (ITDS-GC).
|
CSF Standard Name |
Version |
Approved Date |
|
1.0 |
24/3/2023 |
|
|
1.0 |
24/3/2023 |
|
|
1.0 |
24/3/2023 |
|
|
1.0 |
24/3/2023 |
|
|
1.0 |
24/3/2023 |
Further CSF standards are currently in the process of being reviewed and approved and will be published here once approved. Additional standards in the pipeline include:
- CSF Security Incident Management Standard
- CSF Cryptographic Standard
- CSF Media Sanitisation and Disposal Standard
- CSF IT Security Risk management Standard
- CSF Security Operations Standard
- CSF Physical Security Standard
- CSF Personnel Security Standard
- CSF Identity and Access Management Standard
- CSF Network Security Standard
