Cyber Security Training
With cyber security threats on the rise, we are committed to fostering a security-aware culture and to equipping staff and students with the knowledge to thwart cyber threats.
-
Cyber Hygiene Awareness Videos
Overview
The University sends out security awareness videos that cover various topics in cyber security including:
- Data security
- Data privacy
- Information Protection
- Office Hygiene
- Passwords
- DevSecOps
You will receive and email invitation to watch a short (2-3 minute) video, and answer a simple quiz afterwards.
-
Phishing
Overview
Did you know that 90% of security incidents involved some kind of malicious email such as phishing?
It is critical that University staff have the knowledge to distinguish between legitimate email and suspicious email, and not fall prey to clicking on malicious links, opening potentially dangerous attachments, or responding to fraudulent emails.
Simulated phishing serves two useful purposes for the University: they can (a) identify people who may be more vulnerable to phishing emails and provide just-in-time training (b) provide useful statistics on the proportion of people who are vulnerable and/or report phishing
If you think you have spotted such a simulated phishing email, please report it in the same manner as real phishing emails.
(see below for hints on how to report suspicious emails) -
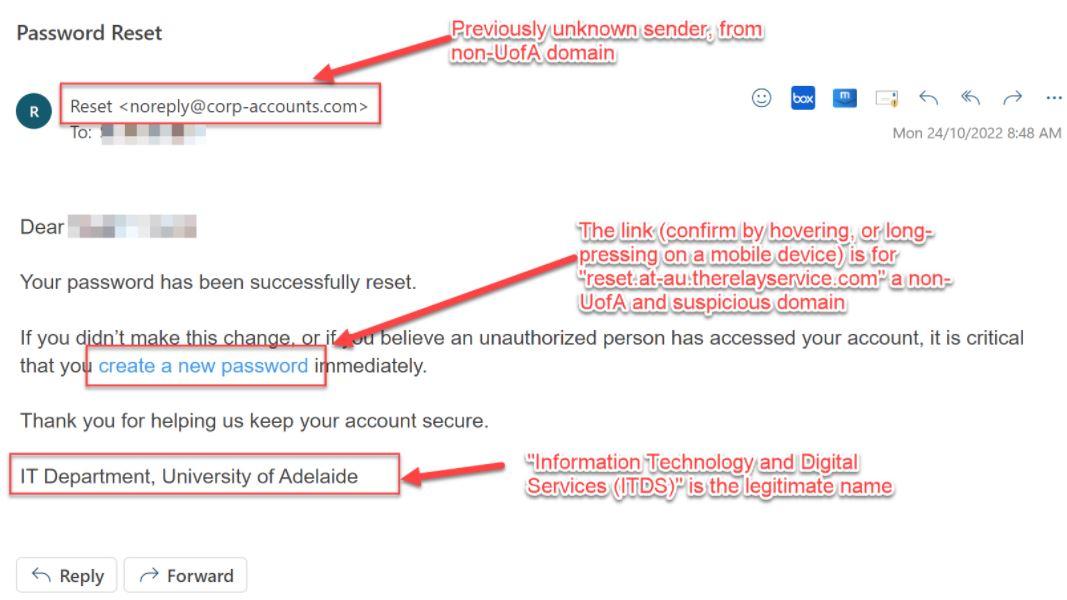
How to spot a phishing email
Suspicious emails can be identified using the following information:
- The sender is not from your usual University of Adelaide senders with a trusted domain such as @adelaide.edu.au
- When you hovered over the link, it will often reveal a non-UoA domain - eg @therelayservice.com; @dodgybrothers.com.au; etc - something you would have never seen before
- Finally, the email may be signed incorrectly - eg "IT Department, University of Adelaide" instead of the correct "Information Technology and Digital Services, the University of Adelaide"
Below is an example of a phishing email, highlighting some things to keep in mind.
Remember - report, don't engage.
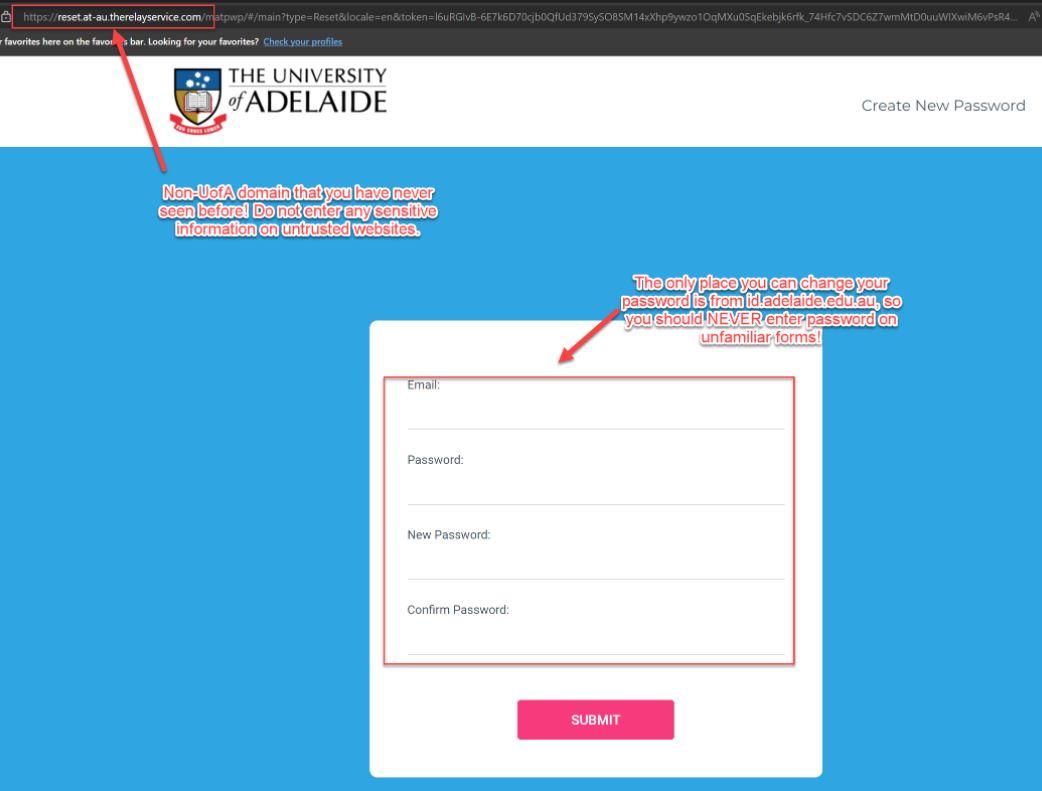
Fake login pages is another potential phishing activity.
Here are some things to keep in mind.
- The fake logon page, even though it has the University of Adelaide logo, has a lot of signs of being non-legitimate
- Look at the URL, this does not have the usual @adelaide.edu.au domain
- The form asks you to enter your details. Currently the only place where you can change your University password is from the Okta login page at https://id.adelaide.edu.au, any other place should be treated with suspicion.